All You Need to Know About DNS Attacks And How to Prevent Them: As networking technologies improve, coupled with an increase in internet usage, we have also seen a rise in the number of data breaches. A study by the University of Maryland shows that cybercriminals attack every 39 seconds with an average of 2,244 attacks every day. It is essential to safeguard your networks and IT systems against these attacks. Among the various types of attacks undertaken by cybercriminals, the DNS attack is quite common.
Hackers can target the DNS in various ways by leveraging a few loopholes. What they do is that they stop you from accessing some of the DNS and lead to a denial of service. The attacks are at the heart of the DNS services and leverage the uses of the DNS to launch severe attacks on the networks. In this article, we will have an overview of the different types of attacks and how to prevent them.
What is a DNS attack?
The attackers can take advantage of the DNS system and launch attacks for nefarious means. It makes genuine visitors unable to access their targeted website. While the DNS system is a bit dated, hackers can attack the DNS service of a network for immoral means. The DNS has a few vulnerabilities that hackers usually exploit to abuse the DNS system. The internal DNS servers store the information about the server names along with the IP addresses. The DNS cache can also be manipulated, and it relays queries from the internal workstations to servers located outside. We will now learn about some of the DNS attacks.
Types of DNS attacks
Flooding with DNS requests
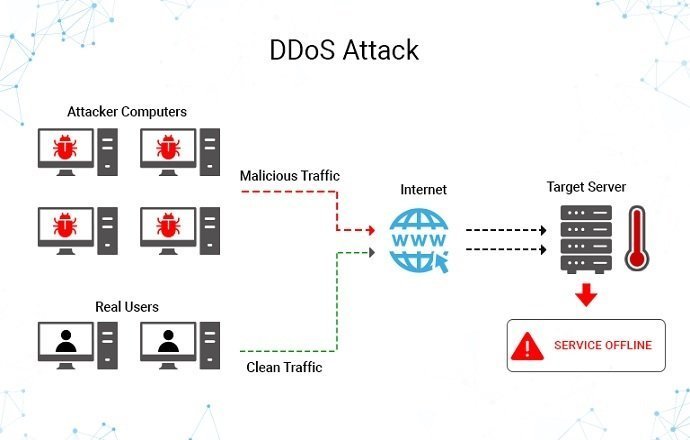
Studies show that there has been almost double the number of DDoS attacks in the first quarter of 2020 than in the same period last year. Hackers may use bots to initiate several DNS requests to target specific servers. As a result, the server has too many requests to address, and legitimate visitors will find that their requests are not getting through.
The attack will be so massive that visitors will not be able to access the site unless they have the IP address of the site in their cache. It is a DDoS attack when you cannot visit the website, even if it may have its presence online. In such an attack, the more the user tries to refresh the page, it leads to a larger number of requests being sent to the server.
A random subdomain attacks
This attack involves making requests for sub-domains that do not even exist. The server will spend resources querying for the sub-domains that do not exist but will only return failure messages. Now, the hacker uses bots to create such requests to any server; it will take up too many resources. As a result, genuine requests will not get through. It is somewhat challenging to segregate which requests are real and which are done by bots. As the DNS recursive server awaits the responses, the genuine queries are faced with a problem.
DNS hijacking
DNS hijacking, or redirection of DNS, is another attack that can affect you. The victims are sent to fake websites as the DNS responses are changed. The hijackers move traffic to fraudulent sites, other than those that are usually visited by users. Hackers can use fraudulent sites for their nefarious means, and that can include falsifying the original websites and extracting sensitive information from the users. DNS hijacking is also used to move traffic to controlled websites for mopping up ad revenues.
Distributed Reflection Denial of Service
It uses third-party open resolvers on the internet. The cybercriminals will send out several requests, but the IP of the source is changed to that of the target. The response of the servers will be forwarded to the modified IP. As a result, the overwhelming traffic floods the target and stops it. Even genuine traffic cannot reach it anymore.
DNS amplification
A DNS amplification attack involves the attacker sending in small queries that lead to large responses. Once this is done for a volley of requests using a bot, it leads to a tremendous amount of traffic being generated. The large volume of responses is then sent to the target address of the target, thereby slowing or overwhelming it.
DNS Tunneling
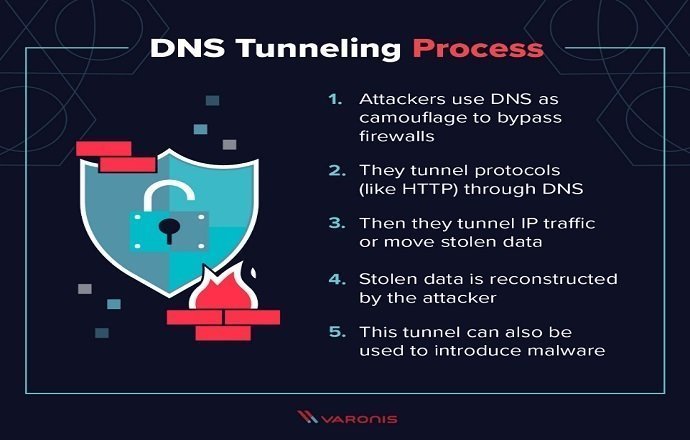
It is a dangerous DNS attack that involves the exploitation of the DNS protocol to transport sensitive information without being detected. The mechanism can be used to shift sensitive data out of your business. With sensitive data going out, it can lead to loss of trust and lawsuits too. The hackers will need access to your business’ networks, which is usually done through phishing. The technique can also be used to place a tunneling client in the target network, which is then used to encode the critical information as a DNS query for a website that is under the hacker’s control.
How to prevent DNS attacks?
Choose a web host wisely
If you wish to ensure the high availability of your site and prevent data breaches, you must choose a renowned web host. You must ensure that you select a hosting plan with the latest encryption standards, SSL authentication, DNS protection, etc. If you are using a content management system, you must utilize the benefits of two-factor authentication and update the software regularly.
Using secure HTTPS
You can force browsers always to load your site using the HTTPS protocol. It will prevent impersonation of your website as the hacker cannot use your website for nefarious means. Businesses must procure single-domain SSL certificates that validate both the website as well as the owner based on the type of certificate chosen. As your website will need authentication and validation by authorized third parties, you can rest assured that hackers cannot copy your site and for that, you have to buy an SSL certificate from Clickssl to secure your websites and beef up your online security.
Keeping the DNS servers up-to-date
It is critical to keep your DNS servers updated which will help you with its security patches and fixes installed. It will also come with the updated security standards. You must run your DNS servers that are updated and support the latest technologies like the RRL that help in data integrity and authentication. You can also set up notifications to make you remember to update the systems and prevent cyberattacks. It will help you to find out any loopholes and plug them well ahead of time.
Undertake audits of the DNS
Most businesses are unaware of the domains that are running, and often they are found to run old software or are vulnerable to attacks. You must run periodic checks by reviewing the records, IPs, and zones. It is in your best interests to undertake an audit of the DNS systems to check whether any updates are pending.
Conclusion
DNS attacks have been increasing over the years as hackers continue to attack IT systems with more sophisticated programs. Businesses must know about the risks of DNS attacks and how they can happen. It will help them to put up robust defenses for their IT networks. It is critical to buy single-domain SSL certificates for advanced protection against DNS attacks. We have also discussed a few other methods to safeguard your systems.
join our telegram it’s free and subscribe to us on youtube.
See more:
Microsoft Windows 11 Latest ISO Full Version Free Download
Basic Termux Android Hacking Commands
How To Become Anonymous On Internet Step to Step




